Think of a cyber security firm as your business’s digital bodyguard. It's the difference between having a simple padlock on your front door and having a full-blown security detail with armoured doors, 24/7 surveillance, and a highly trained team ready to neutralise any threat. They go far beyond basic antivirus software to create a complete security command centre for your entire organisation.
What a Cyber Security Firm Actually Does

A cyber security firm isn’t a product you buy off the shelf; it's a strategic partner. Their entire mission is to shield your most critical assets—your data, your operations, and your hard-earned reputation—from a constantly evolving list of digital threats. They handle the complex security headaches so you can get back to what you do best: running your business.
This kind of partnership is particularly crucial for businesses here in the Philippines. Whether you're a growing small business, a large-scale BPO, or a multi-location hotel, you're a prime target for cybercriminals looking for any weakness to steal data, disrupt your services, or hold your business for ransom.
The Shift from Reactive Fixes to Proactive Defence
Your typical information technology company often works in a break-fix mode. When a server crashes or email goes down, you call them, and they fix it. It's a reactive relationship.
A cyber security firm flips that model on its head. Their job is to be proactive, stopping incidents before they ever get a chance to cause damage. For example, a reactive IT team restores data from a backup after a ransomware attack. A proactive cyber security firm uses advanced email filtering to block the malicious attachment from ever reaching an employee's inbox in the first place.
This forward-thinking approach is built on a few key pillars:
- Constant Monitoring: They keep a vigilant eye on your network around the clock, just like a security guard endlessly patrolling the perimeter of a building. For instance, they would investigate an unusual data transfer to an unknown server at 3 AM, even if no automated alarm is triggered.
- Threat Hunting: They don't just wait for alarms to go off. They actively dive into your systems to find hidden vulnerabilities and potential threats before an attacker does. A practical example is searching for a newly announced software flaw (a "zero-day" vulnerability) across all your company laptops and patching it before criminals can start exploiting it.
- Incident Response: If a breach does happen, they don’t panic. They execute a well-rehearsed plan to contain the damage, kick out the intruder, and get you back to business as quickly as possible. For example, if a user's account is compromised, their first step is to immediately lock the account and disconnect the user's device from the network to prevent the attacker from moving deeper into your systems.
To put it simply, a good cyber security firm moves you away from firefighting and into a state of constant readiness.
| At a Glance: Core Functions of a Cyber Security Firm |
| :— | :— |
| Core Function | What It Means for Your Business (Practical Example) |
| Threat Detection & Prevention | Instead of cleaning up a ransomware mess, they block the malicious email that would have delivered it in the first place. |
| Vulnerability Management | They find the "unlocked window" in your software before a burglar does, patching it to keep intruders out. |
| 24/7 Monitoring & Response | An alert at 2 AM about suspicious activity from an employee's computer is handled by their team, not your own staff. The threat is neutralised while you sleep. |
| Compliance & Reporting | They provide the documentation needed to prove to auditors or clients that you are properly protecting sensitive customer payment data according to PCI DSS standards. |
Ultimately, their role is to ensure your business can keep running smoothly and safely, no matter what threats emerge.
Why External Expertise Is Now Essential
The demand for these specialised security services is exploding in the Philippines, driven by rapid digitalisation and a serious local skills shortage. The Philippine cybersecurity market is expected to hit USD 393.2 million by 2030, but the country has fewer than 300 certified cybersecurity professionals. This huge gap makes it nearly impossible for most companies to build a capable security team in-house.
This is where outsourcing to experts in cybersecurity consulting becomes a strategic necessity. By partnering with a dedicated firm, you immediately gain access to a deep bench of talent, advanced tools, and real-world experience that would take years and a massive budget to build on your own. It's the most effective way to ensure your business stays resilient and secure.
What Does a Cyber Security Firm Actually Do?
So you’ve heard the term, but what services are actually inside that “digital shield” everyone talks about? A professional cyber security firm isn’t just selling a piece of software; they deliver a whole range of specialised services that work in concert. Together, they create layers of defence to protect your business from every conceivable angle.
Think of it like securing a physical building. You wouldn’t just lock the front door and call it a day. You'd have reinforced doors, security cameras, motion sensors, and a team actively monitoring the feeds. Each part has a specific job, but it’s their combined strength that creates real security.
Let's unpack the core services that build this digital fortress and see what they really mean for your day-to-day operations.
Managed Detection and Response (MDR)
Imagine having a dedicated security guard watching your office cameras 24/7/365. They aren’t just sitting there; they’re actively searching for anything unusual, ready to jump into action at a moment's notice. That’s the heart of Managed Detection and Response (MDR).
MDR isn't just another automated alert system that bombards you with notifications. It's a service powered by technology but led by real human experts who hunt for threats, sift through the noise to find what’s real, and take immediate, decisive action to shut down attacks before they can do damage.
For example, say an employee clicks on a phishing email at 10 PM. Malicious software starts trying to encrypt your company’s shared drive. An MDR team would spot this strange file activity instantly, isolate that computer from the network to stop the attack from spreading, and kill the threat—all before your team even arrives for coffee the next morning.
Penetration Testing and Vulnerability Assessments
How can you be sure your security measures actually work? You have to test them. Penetration testing, or "pen testing," is essentially hiring a team of ethical hackers to do their best to break into your systems.
Their entire job is to think like a criminal and find the same weak spots and backdoors that a real attacker would exploit. By finding these gaps in a controlled test, you get a clear, actionable roadmap to fix them before they lead to a catastrophic breach. A practical example would be a pen test on a new e-commerce website before it launches. The testers would try to manipulate prices, access other customers' account data, and bypass payment gateways to ensure no real financial or data loss can occur once the site is live.
By simulating a real-world attack, penetration testing moves your security posture from theoretical to proven. It answers the critical question, "Are we truly secure?" by providing a clear, actionable report on exactly where your defences need to be strengthened.
This is a non-negotiable service for any business with an online presence, especially if you handle sensitive data through e-commerce sites or customer booking portals.
Firewall Management and Security Hardening
Your firewall acts as the digital bouncer for your business network, deciding what traffic gets in and what gets kicked out. But a firewall is only as good as its configuration. An out-of-the-box or poorly managed firewall is like a locked door with the key left hanging in it.
Firewall management is a service where experts take over this critical job. They craft and maintain the rule sets to block malicious traffic while ensuring your legitimate business activities flow smoothly and without interruption.
Hand-in-hand with this is security hardening. This is the process of proactively sealing every potential digital crack and crevice in your network. This includes things like:
- Removing unnecessary software that could become a security risk.
- Disabling old or unused user accounts that attackers could take over.
- Enforcing strong password policies across the entire organisation.
- Tweaking system settings from their default state to a configuration of maximum security.
A classic example is a hotel's public Wi-Fi. Security hardening would involve completely isolating the guest network from the internal network used for payments and reservations. That way, a threat on the guest Wi-Fi can never cross over to touch your critical business systems.
Managed Backups and Disaster Recovery
Let's be realistic: no security system is 100% foolproof. If the worst happens—a devastating ransomware attack or a complete server meltdown—your last line of defence is your data backup. But proper backup management is a lot more complicated than just copying files to an external hard drive.
A managed backup service ensures that your vital business data is backed up consistently, securely, and in a way that allows for a swift recovery. The firm doesn't just "set it and forget it"; they verify the backups are actually working and store them in a secure, often off-site location, protecting them from physical disasters like fires or floods. For instance, they might perform a quarterly test restore of a critical database to a sandbox environment to prove the backup is viable and that the recovery process meets the time outlined in your agreement.
This service is your ultimate safety net. It gives you the peace of mind that no matter what happens, you can restore your operations and get back to business without facing ruinous data loss.
The Growing Urgency for Cybersecurity in the Philippines
The whole conversation around cybersecurity has changed. What used to feel like a problem for massive global companies is now a daily, urgent reality for businesses of all sizes, right here in the Philippines. The simple truth is, if you have a website, keep customer records, or take payments online, you're on a criminal's radar.
Yesterday's defences just don't cut it anymore. Basic antivirus software, which was once a reliable gatekeeper, is now like bringing a simple padlock to a high-tech bank heist. Today's threats are automated, relentless, and built specifically to walk right past those old-school protections. Partnering with a dedicated cyber security firm is no longer a luxury—it’s a fundamental cost of doing business, essential for staying alive and growing.
The Real-World Impact on Local Industries
The fallout from a security breach isn't some abstract concept; it's tangible, expensive, and can paralyse an organisation overnight. The threat isn't just about losing data—it's about losing your ability to operate, your customers' trust, and your position in the market. The rapid digital shift we explored in our guide on technology in the Philippines also gives criminals a much larger area to attack.
Think about these all-too-common scenarios:
- For a BPO: A ransomware attack locks up every single computer, bringing operations to a dead stop for a full week. Suddenly, client contracts are violated, service level agreements (SLAs) are missed, and the damage to your reputation is permanent.
- For a Hotel Chain: A data breach exposes the private and financial details of thousands of guests. The business is now facing massive regulatory fines, a PR disaster, and a flood of lawsuits—not to mention a complete erosion of customer loyalty.
These aren't hypothetical horror stories; they're happening every day. Each one teaches a hard lesson: the cost of a breach is always, without fail, far greater than the investment in preventing it.
A Threat Landscape on the Rise
The sheer volume and sophistication of attacks hitting Philippine businesses are climbing at a frightening pace. This surge is making partnerships with cyber security firms more critical than ever. Recent studies on the local threat landscape show private organisations have seen around a 30% increase in ransomware incidents and a staggering 49% rise in web-based threats. This year alone, Philippine networks have already weathered more than 4.1 million password-guessing IT attacks. That number is a loud-and-clear signal of just how vulnerable poorly configured or unmonitored systems really are. You can dig deeper into the data over at Security Quotient's report on the Philippine cyber threat landscape.
This spike is fuelled by automated tools that constantly sweep the internet for weak spots. We're not talking about a lone hacker in a dark room. These are sophisticated, organised efforts using scripts to find and exploit vulnerabilities on an industrial scale. A practical example is an automated script that scans thousands of websites per minute, looking for a specific, unpatched vulnerability in a popular e-commerce plugin. When it finds a match, it automatically exploits it.
Your business doesn't have to be a major corporation to be a target. Cybercriminals often prefer smaller businesses because they are "softer targets"—possessing valuable data but lacking the robust defences of a larger enterprise. This makes proactive security a matter of survival, not scale.
A professional cyber security firm is your shield against this rising tide. They bring the advanced tools, round-the-clock monitoring, and expert teams needed to spot and stop these threats before they can do any real damage. In today's dangerous digital world, that proactive defence is the only effective way to build resilience, protect your revenue, and make sure your business can operate safely.
Your Practical Checklist for Choosing a Security Partner
Picking the right cyber security firm is easily one of the most critical decisions you'll make for the future of your business. This isn't just about hiring another vendor—it's about finding a long-term partner you can trust, one who understands your specific operational realities and has the expertise to back it up. This guide will give you the right questions to ask so you can cut through the sales pitches and choose the team best equipped to protect you.
Outsourcing security is fast becoming the norm here in the Philippines, and for good reason. A recent study, the 2025 Cisco Cybersecurity Readiness Index, found that a massive 98% of local businesses are planning to increase their security budgets. Even more telling, 43% are already partnering with managed service providers, showing that teamwork is the new standard for a solid defence. This shift makes your selection process more important than ever. You can read more about these findings from Cisco to see just how the local landscape is changing.
Think of your security posture like this:
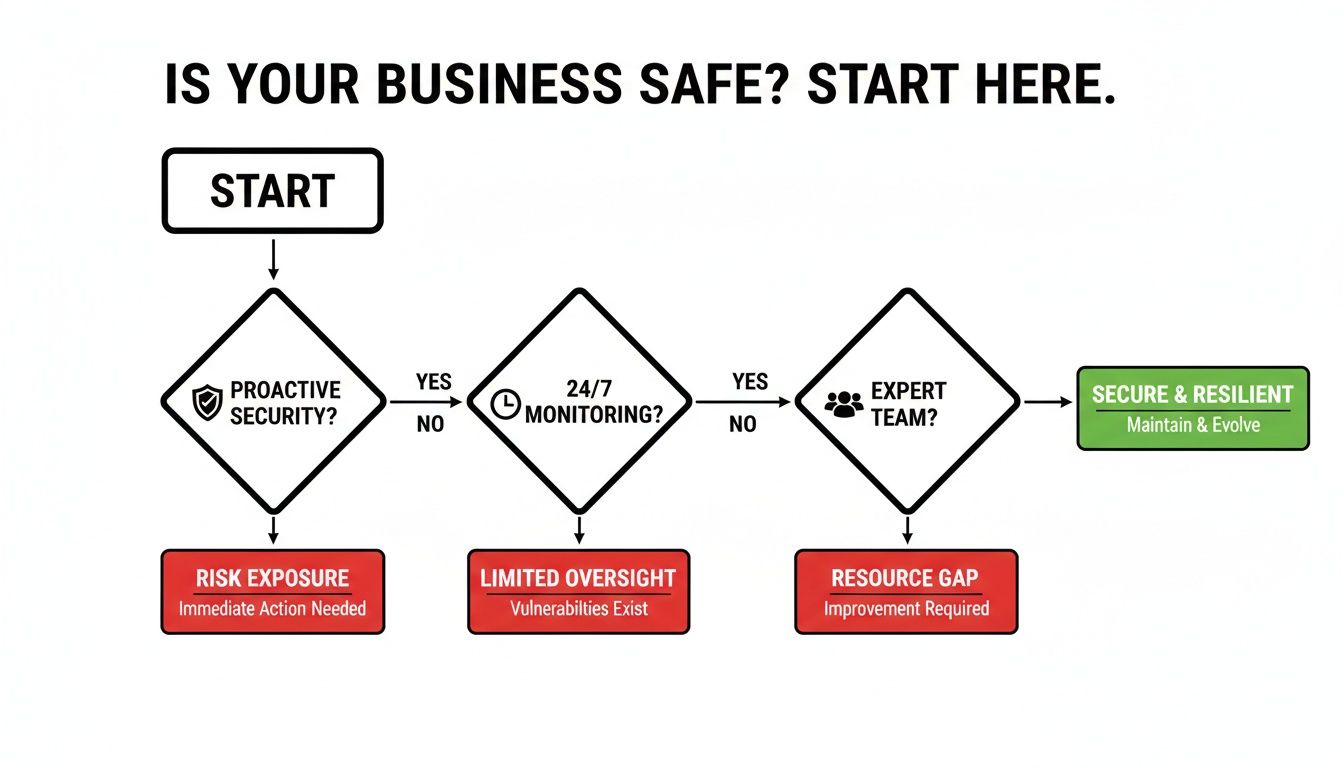
As the chart shows, real business resilience isn't about a single product. It’s a combination of proactive measures, constant monitoring, and expert oversight—all things a great security partner should deliver.
Verifiable Industry Experience
Knowing security theory is one thing, but having battled threats in the real world is something else entirely. A firm that’s already protected businesses like yours will know your industry's specific threats, compliance headaches, and operational quirks inside and out.
Don't let them get away with vague promises. You need to dig deeper.
- Ask this directly: "Can you show us case studies or connect us with references from clients in our industry, especially ones our size?"
- For example: If you run a BPO, you'd ask for proof of how they've handled data privacy compliance for another call centre. If you manage a hotel, you’d ask how they've secured guest Wi-Fi networks without compromising sensitive booking data. This is how you confirm they've solved your exact problems before.
Relevant Certifications and Credentials
Certifications aren't just fancy badges for a website. They're independent proof that a team has the technical chops and is committed to staying current. It shows they invest in their people to keep up with the bad guys.
Look for credentials that actually matter for the services you need:
- CISSP (Certified Information Systems Security Professional): This is the gold standard, a globally recognised certification for high-level security management and expertise.
- CEH (Certified Ethical Hacker): This proves they know how to think like a hacker, which is absolutely essential for effective penetration testing.
- Vendor-Specific Certifications: Seeing certifications from brands like Fortinet or Cisco means they have deep, hands-on knowledge of the actual hardware and software that will be protecting your network.
Clear Service Level Agreements (SLAs)
A Service Level Agreement, or SLA, is your guarantee on paper. It sets clear expectations and spells out precisely what the firm will do when a crisis hits. If a potential partner has a vague SLA—or none at all—that’s a huge red flag.
This document should leave no room for interpretation when you need help the most. For example, a good SLA will state a "15-minute response time for critical incidents," defining a critical incident as something like active ransomware encryption or a confirmed data breach. It will also specify that "response" means an engineer is actively working on the problem, not just sending an automated email.
Think of the SLA as the backbone of your partnership. It turns promises into contractual obligations. When an incident happens and every second counts, you'll know exactly how fast they're required to act.
Get specific with your questions about their process:
- How do you classify a "critical security incident" versus a "minor alert"?
- What is your guaranteed response time for a critical incident? Does that just mean an email reply, or does it mean someone is actively working on the problem?
- Walk me through your step-by-step process, from the moment an alarm goes off to the final resolution.
Support for Your Entire Infrastructure
Modern security isn't just about software. It's about protecting your entire tech stack—servers, firewalls, laptops, everything. A great security firm can manage both the hardware and the software, creating a single, seamless shield around your business.
This is especially critical if you need a provider who can also supply and manage physical devices across different locations. A partner who can act as your trusted security system supplier while also handling the 24/7 monitoring offers a much stronger, more cohesive solution. Ask them if they offer hardware leasing, on-site support, and replacement services as part of their packages.
Transparent Pricing Models
Finally, you have to understand what you're paying for. Hidden fees and confusing contracts can ruin a partnership fast. A trustworthy firm will be completely upfront about its pricing and what’s included at every level. When looking at your options, checking out a comparison of the best cybersecurity consulting firms can provide a clearer picture of market rates and service packages.
Understanding the common pricing structures is key to finding a plan that fits your budget and avoids nasty surprises down the road.
Comparing Cyber Security Firm Pricing Models
This table breaks down the typical pricing models you'll encounter. Use it to figure out which approach makes the most sense for your business needs and financial planning.
| Pricing Model | Best For | Potential Pros | Potential Cons |
|---|---|---|---|
| Flat-Rate Subscription | Businesses needing predictable monthly costs and comprehensive, ongoing support. | Budget-friendly and easy to plan for. Often includes a wide range of services in one fee. | May include services you don't fully need. Less flexibility for one-off projects. |
| Per-Device/Per-User | Companies with a clear number of assets to protect, like SMBs or those with a fixed employee count. | Scales directly with your business size. You only pay for what you're protecting. | Costs can fluctuate if your team or device count changes frequently. Can become expensive for large organisations. |
| Tiered Packages | Organisations that want to choose a service level (e.g., Basic, Pro, Enterprise) based on their needs. | Clear options and easy to upgrade or downgrade as your needs change. | The "basic" tier might lack critical services, forcing an upsell. Features can be bundled inflexibly. |
| Ad-Hoc/Consulting | Businesses needing one-time services like a security audit, penetration test, or incident response. | Pay only for the specific service you need. Ideal for project-based work. | Can be very expensive for emergency services (incident response). Doesn't include ongoing monitoring. |
Choosing the right model is just as important as choosing the right partner. Make sure their pricing aligns with how your business operates.
By following this checklist, you can get past the marketing fluff and make a decision based on proven expertise and clear commitments. You'll be choosing a true partner, not just another vendor.
Common Red Flags When Hiring a Security Provider
Choosing the wrong cyber security firm can be just as damaging as a data breach itself. A bad partnership doesn't just waste your budget; it leaves you dangerously exposed while giving you a false sense of security. To avoid a costly mistake, you need to learn how to spot the warning signs of a provider who’s more interested in a quick sale than your long-term protection.
The first and most obvious red flag is any promise of “100% guaranteed protection.” Let’s be clear: in cybersecurity, there are no absolutes. A trustworthy firm knows this and will talk about building resilience and reducing risk, not selling you an unbreakable shield. Anyone guaranteeing you'll never have an incident is selling a fantasy, not a professional service.
Another major warning sign is a rigid, one-size-fits-all service package. Your business is unique, with its own workflows, tech stack, and specific risks. A provider pushing a generic plan without first taking the time to understand your operations isn't a partner; they're a reseller. For example, a security package designed for a retail store won't address the specific compliance needs of a healthcare clinic handling sensitive patient data. A good partner customises their approach.
Unrealistic Promises and Vague Language
Be wary of providers who hide behind confusing jargon instead of focusing on clear business outcomes. If they can't explain in plain English how their services will protect your specific assets or reduce your risk of downtime, it’s a sign they either lack true expertise or are trying to obscure their process.
A great security partner builds confidence through clarity. They translate technical actions into business impact, ensuring you understand exactly what you are paying for and why it matters to your bottom line. Confusion is a sales tactic, not a security strategy.
Their communication during the initial vetting process says a lot. If they're slow to respond or give you vague answers now, just imagine what it will be like during a real crisis when every second is critical.
Lack of Transparency in Contracts and Costs
Finally, comb through their contracts and pricing models with a fine-tooth comb. A reliable firm will be completely upfront about all potential costs—setup fees, monthly retainers, and any extra charges for emergency incident response. There should be no surprises.
Pay close attention to these common contractual red flags:
- Hidden Fees: Vague line items or overly complex clauses are often designed to hide unexpected bills down the road. For example, a contract might not specify that restoring data from backups incurs a separate, high hourly rate.
- Long Lock-in Periods: Unusually long contracts with steep penalties for early termination are a way to trap you with an underperforming provider.
- Undefined Scope: The contract should clearly define what services are included and what counts as an "out-of-scope" request that will cost you extra. For instance, is adding a new employee's laptop to the monitoring service included in your fee or does it trigger an additional charge?
By staying vigilant for these warning signs, you can filter out the opportunistic vendors and find a true cyber security partner committed to genuinely protecting your business.
Your Top Questions About Cyber Security Firms, Answered
Stepping into the world of cybersecurity can feel a bit overwhelming, and it's natural to have questions. Let's cut through the noise and tackle some of the most common concerns we hear from business owners here in the Philippines. My goal is to give you clear, straightforward answers so you can make decisions with confidence.
Is My Small Business Really a Target for Cyberattacks?
Yes. I can't stress this enough. There’s a persistent and dangerous myth that attackers only go after the big players. The reality is that criminals often see small and medium-sized businesses (SMBs) as the perfect targets—you have valuable data, but often without the fortress-like defences of a large corporation.
Think of it this way: mid-size firms are in a tough spot. You're big enough to be a profitable target, but you likely don't have the massive security budgets of an enterprise. A single attack can be devastating.
- Here's a real-world scenario: Imagine a small accounting firm in Manila. Two weeks before the tax deadline, ransomware hits and encrypts all their client files. They're suddenly faced with an impossible choice: pay a huge ransom they can't afford, or go out of business because they can't serve their clients.
This is where a modern cyber security firm comes in. We offer scalable, affordable solutions that give you access to the same level of protection as the big guys, effectively levelling the playing field.
What’s the Difference Between IT Support and a Cyber Security Firm?
The simplest way to explain it is reactive versus proactive.
Your traditional IT support team is like your digital mechanic. When something breaks—a printer won’t connect, an application crashes—you call them, and they fix it. A cyber security firm, on the other hand, is your digital security detail. Our job is to stop things from ever breaking in the first place.
Your IT support gets a call when your server is down. A cyber security firm works 24/7 to make sure an attacker never gets the chance to take it down. We’re focused on risk reduction and threat prevention, not just break-fix repairs.
Let's look at how each would handle a common situation:
- IT Support: An employee reports they can't access their email. The IT helpdesk troubleshoots the account, resets the password, and closes the ticket. Problem solved.
- Cyber Security Firm: Our monitoring system flags an impossible login—someone trying to access that same email from another country just minutes after the employee logged in from Makati. We immediately block the IP, force a password reset, and start investigating if any other accounts were targeted. We prevent the breach before it even happens.
Of course, the best providers often bring both under one roof, offering managed IT services alongside security for a complete, headache-free solution.
How Much Should I Budget for Cybersecurity?
There's no one-size-fits-all answer here. The cost really depends on your company's size, how many people and devices you need to protect, and the specific services you need. Most firms, including us, use a predictable monthly retainer model. This helps you budget properly and avoid a sudden, massive bill when an emergency strikes.
But instead of focusing just on the monthly fee, I encourage you to think about the potential cost of doing nothing. The financial fallout from a single breach—think business downtime, data recovery fees, potential fines, and long-term damage to your reputation—almost always eclipses the investment in proactive security.
The smartest first step is to get a customised assessment. A good firm will take the time to understand your specific vulnerabilities and how your business operates before giving you a detailed quote. That way, you’re only paying for the protection you actually need.
Can a Single Firm Handle My Network Setup and My Security?
Absolutely, and frankly, it’s the best way to do it. When the same team that runs your structured cabling and configures your firewalls is also the one providing 24/7 monitoring, security isn't just an add-on; it's baked into your foundation from the very beginning.
This integrated approach creates a much more seamless and resilient infrastructure.
- Think about this: A BPO is expanding to a new office floor. An integrated provider starts by designing and installing the network cabling for peak performance. Next, they supply and configure the firewalls with rules specifically tailored for the BPO's software. From the second that new network goes live, their Security Operations Centre is already monitoring it.
This unified strategy eliminates security gaps that can appear when you have multiple vendors trying to coordinate. It simplifies your life and is often more cost-effective in the long run.
Ready to build a resilient and secure foundation for your business? REDCHIP IT SOLUTIONS INC. provides integrated IT and cybersecurity services, from network setup and hardware leasing to 24/7 monitoring and support, ensuring your organisation can scale safely and confidently. Learn more and request your customised security assessment today.





